Understanding Harvest Now, Decrypt Later Attacks: The Silent Threat to Your Data Security
In an increasingly interconnected digital world, data security has never been more critical ^1. As organizations adopt robust encryption measures to protect their valuable information assets, a new threat has emerged on the horizon - one that doesn't aim to break today's encryption but patiently waits for tomorrow's technology to do the job. This threat is known as "Harvest Now, Decrypt Later" (HNDL), and it represents one of the most significant challenges in the post-quantum era of cybersecurity.
What Are Harvest Now, Decrypt Later Attacks?
Harvest Now, Decrypt Later is a sophisticated surveillance and attack strategy where adversaries collect and store currently encrypted data with the intention of decrypting it once quantum computing technology becomes powerful enough to break today's encryption standards. The premise is simple yet alarming: what can't be decrypted today will potentially become vulnerable tomorrow.
These attacks are particularly concerning because they're happening right now, even though the full impact won't be felt until quantum computers reach sufficient computational power - a timeline often referred to as "Q-Day" or "Y2Q" (Year to Quantum) ^2.
How HNDL Attacks Work
The HNDL attack methodology consists of three primary stages :
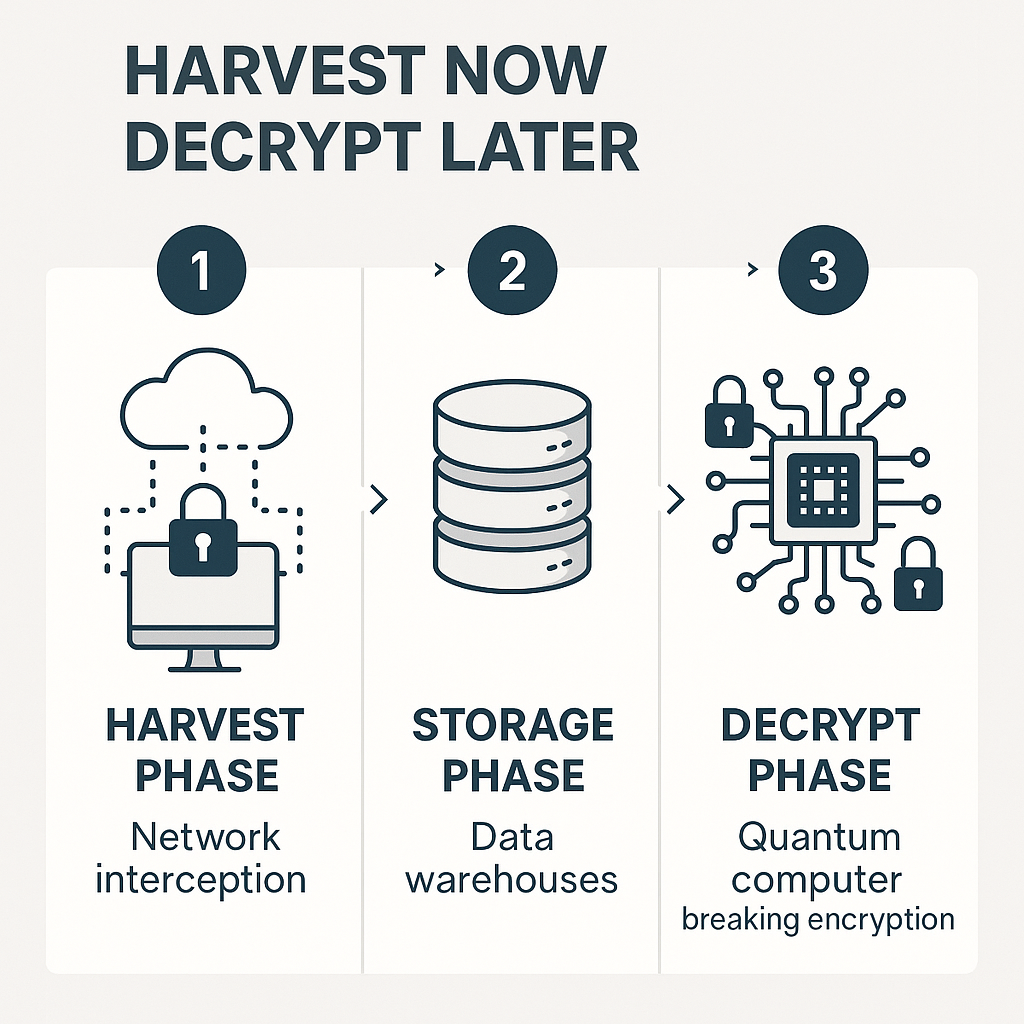
The three phases of a harvest now, decrypt later attack.
The Harvest Phase
In this initial stage, adversaries focus on intercepting and collecting encrypted data through various means including passive network monitoring, man-in-the-middle attacks, compromising data repositories, BGP hijacking to reroute internet traffic, and exploiting system vulnerabilities. The attackers aren't concerned with decrypting the information immediately - their goal is simply to amass as much valuable encrypted data as possible for future exploitation.
The Storage Phase
Once harvested, the encrypted data is securely stored, potentially for years or even decades. This storage phase requires minimal resources compared to the computational power needed for decryption. Adversaries must only ensure the data remains intact and accessible when quantum computing technology matures.
The Decrypt Phase
The final stage will occur when quantum computers become sufficiently powerful to break current encryption algorithms using quantum algorithms like Shor's algorithm ^3. This quantum breakthrough will enable attackers to decrypt previously harvested data and potentially gain access to sensitive information that was protected years earlier.
The Quantum Computing Threat Landscape
The critical question becomes: how long do we have before quantum computers can break our current encryption? According to recent forecasts as of 2025, cryptographically relevant quantum computers could arrive as early as 2030-2035, within the next 5-10 years.
Several significant developments in 2025 have highlighted the rapid advancement of quantum computing ^5. Google's director of Quantum AI has expressed optimism that it could be just five years before quantum computers become the preferred choice for certain computational tasks ^4. Recent achievements in logical qubits and specialized quantum hardware have accelerated this timeline.

A multi-tiered cryogenic cooling system for a quantum computer.
Vulnerable Encryption Methods
Not all encryption algorithms are equally vulnerable to quantum attacks. The primary concern centers around public-key encryption methods that rely on mathematical problems quantum computers can solve efficiently.
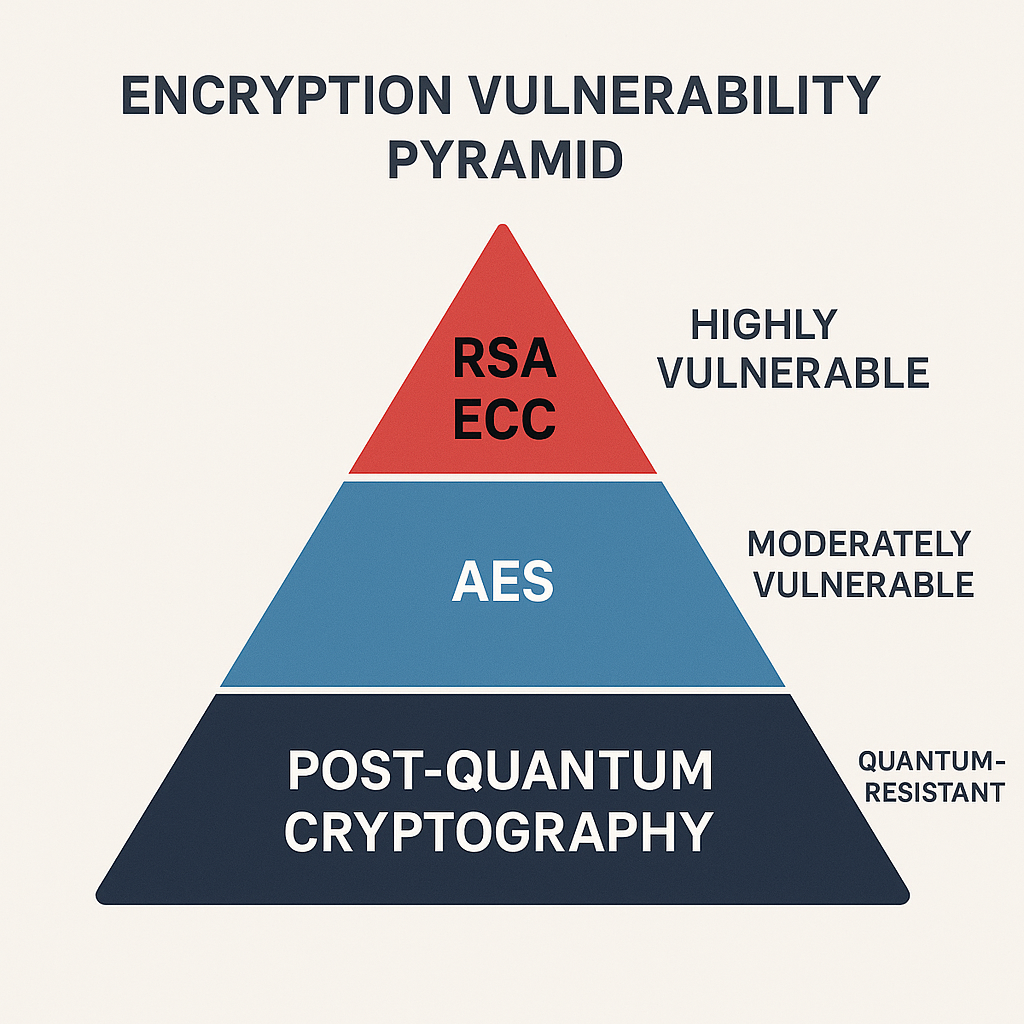
Encryption vulnerability pyramid showing different encryption levels against quantum computing attacks.
Highly Vulnerable Algorithms
RSA encryption, used extensively for secure communications, relies on the difficulty of factoring large prime numbers—a problem that Shor's quantum algorithm can solve efficiently. Elliptic Curve Cryptography (ECC), common in mobile devices and VPNs, is also vulnerable to quantum attacks. Diffie-Hellman key exchange algorithms will be compromised by quantum computing capabilities.
Moderately Secure Methods
Symmetric encryption like AES offers better quantum resistance but requires larger key sizes (256-bit or greater) to maintain security in the quantum era . Hash functions are generally more resistant to quantum attacks but may require updates for long-term security .
Industries and Data Types at Greatest Risk
HNDL attacks target data with long-term value that remains sensitive for years or decades. Financial institutions face risks to customer records, banking transactions, and investment strategies. Healthcare organizations must protect medical histories and personal health information that can be used for identity theft or blackmail .
Government and defense sectors are particularly vulnerable due to classified communications, diplomatic cables, and military strategies that retain strategic value indefinitely . Intellectual property including trade secrets, proprietary algorithms, and research data can maintain commercial value for decades.
Evidence of Current HNDL Activity
Most cybersecurity experts believe that HNDL attacks are primarily conducted by sophisticated threat actors with substantial resources, particularly nation-state actors. Several incidents in recent years suggest these attacks may already be underway.
In 2016, Canadian internet traffic to South Korea was mysteriously rerouted through China. Similar incidents occurred in 2019 with European mobile phone traffic experiencing suspicious rerouting. In 2020, data from Google, Amazon, Facebook, and over 200 other networks was redirected through Russia.
The Path to Protection: Post-Quantum Cryptography
The most effective defense against HNDL attacks is implementing post-quantum cryptography (PQC)—encryption algorithms designed to withstand attacks from both classical and quantum computers. In August 2024, NIST released its first set of PQC standards after an extensive eight-year evaluation process.
These standards include lattice-based cryptography with ML-KEM for key encapsulation and ML-DSA for digital signatures, hash-based cryptography including SLH-DSA for digital signatures, and code-based cryptography with HQC as a backup algorithm. Organizations should begin planning their migration to these quantum-resistant algorithms now, before quantum computers become capable of breaking current encryption ^7.
Best Practices for HNDL Protection
Organizations must take immediate action to protect against these silent threats. The first step involves conducting a comprehensive cryptographic inventory to identify all instances of cryptographic use across infrastructure . Data classification by sensitivity and longevity helps prioritize protection for information that needs to remain confidential for more than 3-5 years.
Immediate Protective Measures
Implementing stronger symmetric encryption by moving to AES-256 wherever possible provides enhanced security against quantum attacks . Using pre-shared keys for critical communications through secure, out-of-band channels eliminates vulnerable asymmetric key exchanges . Adopting Perfect Forward Secrecy (PFS) with ephemeral session keys ensures that compromise of long-term keys doesn't enable decryption of past communications .
Strategic Planning
Developing a comprehensive PQC migration roadmap creates a timeline for transitioning all systems to quantum-resistant cryptography. Requesting PQC roadmaps from security vendors ensures they have clear plans for implementing post-quantum solutions. Considering hybrid cryptographic approaches that combine classical and post-quantum algorithms provides added security during the transition period ^9.
Building Long-Term Resilience
Organizations must build crypto-agility to quickly adapt to new cryptographic algorithms without major system overhauls ^8. Planning for regular cryptographic updates establishes processes for reviewing and updating implementations as standards evolve. Participating in standards development through industry groups helps shape post-quantum best practices.
The Business Case for Action
The urgency of HNDL protection varies by organization based on security needs and risk tolerance ^6. This urgency depends on three primary factors: shelf-life time (how long data must remain secure), migration time (how long system upgrades take), and threat timeline (when quantum computers become viable).
Organizations with long-lived sensitive data face the greatest risk and should prioritize immediate action . Each day of delay potentially allows attackers to harvest more information for future decryption.
SecQuant: Your Partner in Post-Quantum Security
At SecQuant, we provide cutting-edge post-quantum cryptography solutions to protect your critical assets and ensure long-term data security in the quantum era. Our solutions implement NIST-standardized post-quantum algorithms, provide seamless migration paths from current cryptographic systems, and enable crypto-agility to adapt to evolving standards.
We deliver comprehensive security against both current and future threats while offering quantum-resistant protection for your most sensitive data. Our expertise helps organizations navigate the complex transition to post-quantum cryptography with confidence and strategic planning.
Conclusion
Harvest Now, Decrypt Later attacks represent a paradigm shift in cybersecurity threat modeling. The encrypted data being harvested today could be decrypted tomorrow, with potentially devastating consequences for organizations and individuals alike.
The time to act is now. By understanding the threat, implementing immediate protective measures, and planning for a transition to post-quantum cryptography, organizations can safeguard their valuable information assets against this emerging threat landscape. In an era where data represents one of your most valuable assets, ensuring its long-term security requires forward-thinking strategies and technologies designed for the quantum age.
Don't wait until it's too late—the harvest is already underway.
⁂




